Azure VPN Gateway
Azure provides a VPN Gateway that can create IPSec tunnels between endpoints. This can be used to create a secure tunnel to FoxTech DEFEND over which syslog from other devices can be sent.
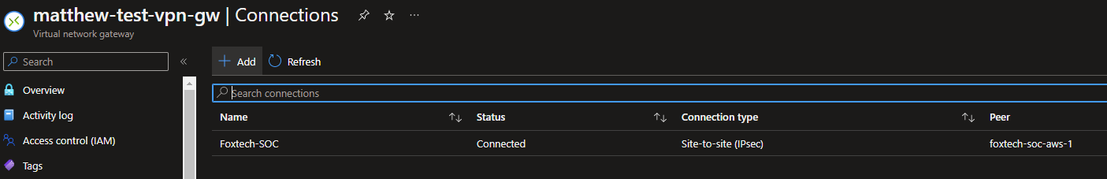
The following configuration is needed on the Azure side, this can all be done using the portal
1. A Virtual Network. This can already exist, if so the VN that contains the resources to be accessed should be chosen.
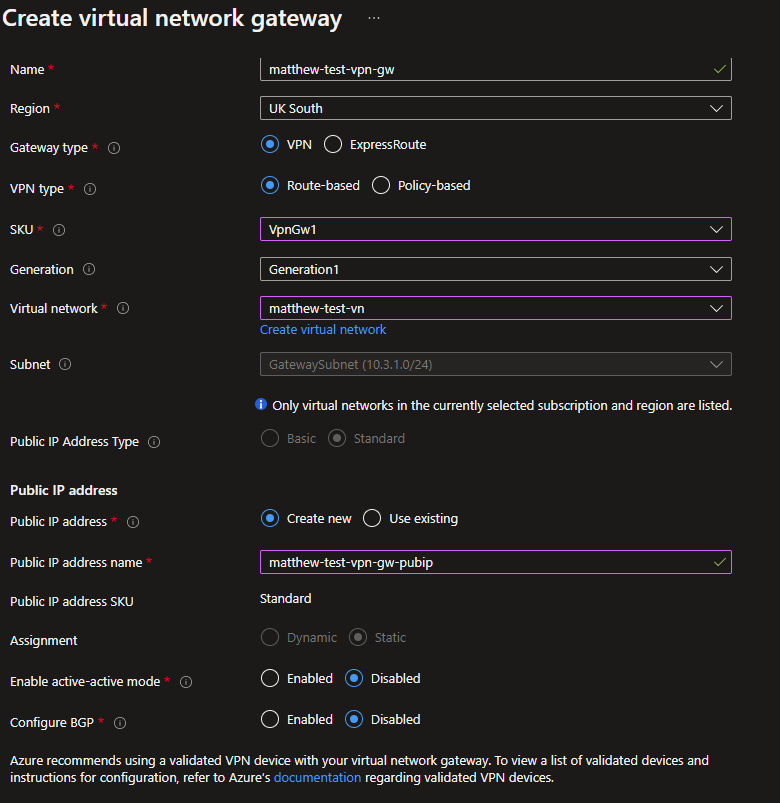
2. A VPN Gateway with a public IP and a dedicated VPN Gateway Subnet. Note that in order to support DEFEND's IKE encryption standards at least VPNGw1 SKU must be chosen Microsoft VPN Gateway Pricing as “more than basic” only allows for custom IPSEC profiles.
This allows up to 10 Site-to-Site IPSec VPNs without any AZ failover. Depending on the Azure configuration other SKUs or custom BGP configurations may be necessary:
Public IP
{
"name": "defend-test-vpn-gw-pubip",
"id": "/subscriptions/12345678-sampleresourceid/resourceGroups/DEFEND-RG/providers/Microsoft.Network/publicIPAddresses/defend-test-vpn-gw-pubip",
"etag": "W/\"12345678-sampleresourceid\"",
"location": "uksouth",
"properties": {
"provisioningState": "Succeeded",
"resourceGuid": "12345678-sampleresourceid",
"ipAddress": "20.162.224.214",
"publicIPAddressVersion": "IPv4",
"publicIPAllocationMethod": "Static",
"idleTimeoutInMinutes": 4,
"ipTags": [],
"ipConfiguration": {
"id": "/subscriptions/12345678-sampleresourceid/resourceGroups/Matthew-RG/providers/Microsoft.Network/virtualNetworkGateways/defend-test-vpn-gw/ipConfigurations/default"
}
},
"type": "Microsoft.Network/publicIPAddresses",
"sku": {
"name": "Standard"
}
}
VPN Gateway
{
"name": "defend-test-vpn-gw",
"id": "/subscriptions/12345678-sampleresourceid/resourceGroups/Matthew-RG/providers/Microsoft.Network/virtualNetworkGateways/defend-test-vpn-gw",
"etag": "W/\"12345678-sampleresourceid\"",
"type": "Microsoft.Network/virtualNetworkGateways",
"location": "uksouth",
"tags": {},
"properties": {
"provisioningState": "Updating",
"resourceGuid": "12345678-sampleresourceid",
"enablePrivateIpAddress": false,
"ipConfigurations": [
{
"name": "default",
"id": "/subscriptions/12345678-sampleresourceid/resourceGroups/Matthew-RG/providers/Microsoft.Network/virtualNetworkGateways/defend-test-vpn-gw/ipConfigurations/default",
"etag": "W/\"12345678-sampleresourceid\"",
"type": "Microsoft.Network/virtualNetworkGateways/ipConfigurations",
"properties": {
"provisioningState": "Updating",
"privateIPAllocationMethod": "Dynamic",
"publicIPAddress": {
"id": "/subscriptions/12345678-sampleresourceid/resourceGroups/Matthew-RG/providers/Microsoft.Network/publicIPAddresses/defend-test-vpn-gw-pubip"
},
"subnet": {
"id": "/subscriptions/12345678-sampleresourceid/resourceGroups/Matthew-RG/providers/Microsoft.Network/virtualNetworks/defend-test-vn/subnets/GatewaySubnet"
}
}
}
],
"virtualNetworkGatewayPolicyGroups": [],
"sku": {
"name": "VpnGw1",
"tier": "VpnGw1",
"capacity": 2
},
"gatewayType": "Vpn",
"vpnType": "RouteBased",
"enableBgp": false,
"activeActive": false,
"bgpSettings": {
"asn": 0,
"peerWeight": 0,
"bgpPeeringAddresses": [
{
"ipconfigurationId": "/subscriptions/12345678-sampleresourceid/resourceGroups/Matthew-RG/providers/Microsoft.Network/virtualNetworkGateways/defend-test-vpn-gw/ipConfigurations/default",
"defaultBgpIpAddresses": [],
"customBgpIpAddresses": []
}
]
},
"vpnGatewayGeneration": "Generation1"
}
}
3. A “LocalNetworkGateway” which defines the subnets and the target public IP (as seen by Azure):
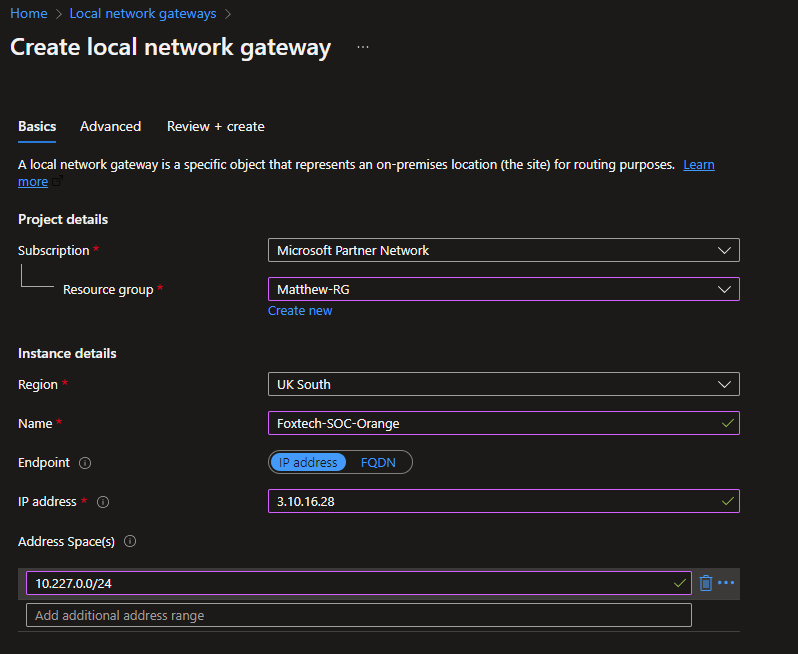
{
"name": "foxtech-soc-aws-1",
"id": "/subscriptions/12345678-sampleresourceid/resourceGroups/Matthew-RG/providers/Microsoft.Network/localNetworkGateways/foxtech-soc-aws-1",
"etag": "W/\"12345678-sampleresourceid\"",
"type": "Microsoft.Network/localNetworkGateways",
"location": "uksouth",
"properties": {
"provisioningState": "Succeeded",
"resourceGuid": "12345678-sampleresourceid",
"localNetworkAddressSpace": {
"addressPrefixes": [
"10.227.0.0/24"
]
},
"gatewayIpAddress": "to be provided"
}
}
4. Next, create a connection on the VPN Gateway:

{
"name": "Foxtech-SOC",
"id": "/subscriptions/12345678-sampleresourceid/resourceGroups/Matthew-RG/providers/Microsoft.Network/connections/Foxtech-SOC",
"etag": "W/\"12345678-sampleresourceid\"",
"type": "Microsoft.Network/connections",
"location": "uksouth",
"properties": {
"provisioningState": "Updating",
"resourceGuid": "12345678-sampleresourceid",
"virtualNetworkGateway1": {
"id": "/subscriptions/12345678-sampleresourceid/resourceGroups/Matthew-RG/providers/Microsoft.Network/virtualNetworkGateways/defend-test-vpn-gw"
},
"localNetworkGateway2": {
"id": "/subscriptions/12345678-sampleresourceid/resourceGroups/Matthew-RG/providers/Microsoft.Network/localNetworkGateways/foxtech-soc-aws-1"
},
"connectionType": "IPsec",
"connectionProtocol": "IKEv2",
"routingWeight": 0,
"sharedKey": "(REMOVED)",
"enableBgp": false,
"useLocalAzureIpAddress": false,
"usePolicyBasedTrafficSelectors": false,
"ipsecPolicies": [],
"trafficSelectorPolicies": [],
"ingressBytesTransferred": 0,
"egressBytesTransferred": 0,
"dpdTimeoutSeconds": 0,
"connectionMode": "Default"
}
}
5. Now create a custom IPSec policy attached to that connection that will comply with our requirements:
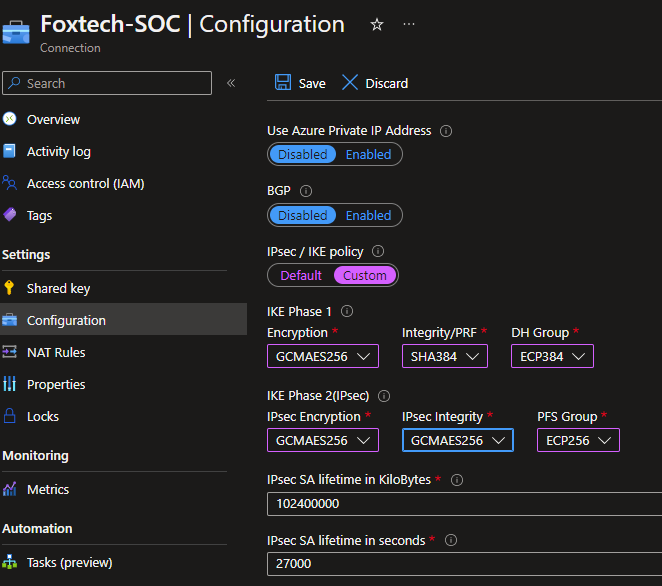
6. At this point the Site-to-Site tunnel will attempt to establish itself but will fail as the public IP address is not allowed on the AWS (SOC) site.
7. Update soc-ansible to add an additional site for the appropriate client & run
8. Update soc-aws to add an additional ipsec_ip for the client & run.
9. After those 3 steps are run, the VPN should show as “connected” on the Azure portal when traffic from either side attempts to cross: