Azure
DEFEND collects Azure logs from an Azure Storage Bucket. You'll need to create a storage bucket, configure Azure to send the logs there, then grant DEFEND access to fetch the logs.
Create Storage Account
First create an Azure Storage Account for storing the exported log files:
Resource Group: FoxTech-SOC-RG
Storage name: foxtechsoc
- Standard performance
- Region: UK South
- Local redundant storage
- Storage Account: foxtech-soc
- Add a rule:
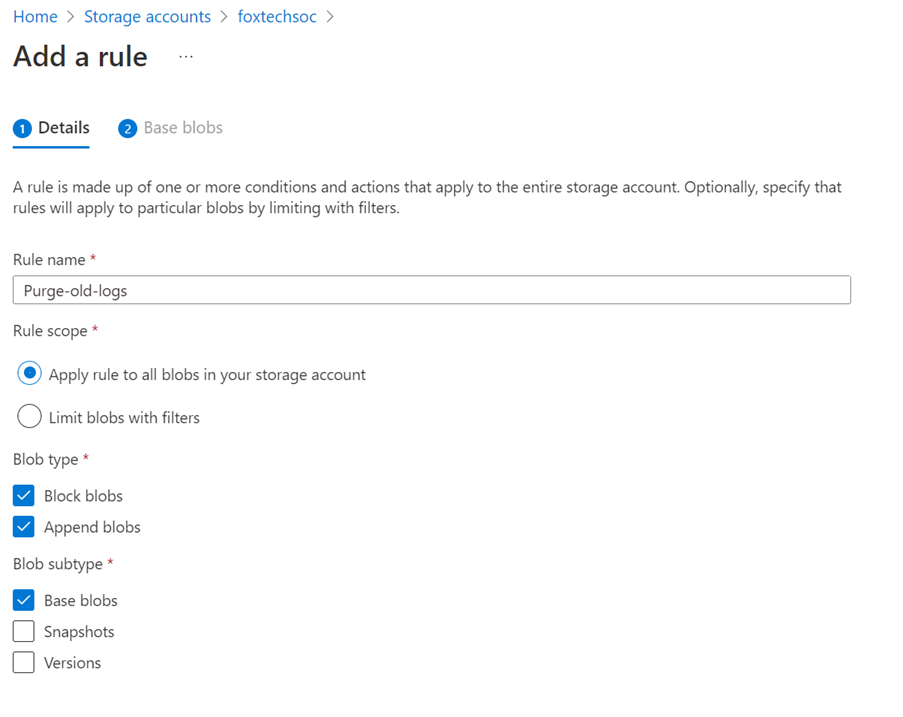
- If blob was last modified more than 14 days ago, then Delete the blob
Grant access
Now grant DEFEND access to the Storage Account:
Add SOC IP Address:
- Go to Storage Account: foxtechsoc
- Security + networking > Networking
- Firewall: Ask FoxTech support for the DEFEND Log Collector IP you've been allocated.
Collect Storage Access Keys, and provide to FoxTech SOC
Export logs
Finally configure Azure to export logs to the storage acccount.
- Portal.azure.com
- Monitor > Activity Log > Export Activity Logs
- Select Subscription to monitor
- Add Diagnostics setting
- Set name to: “FoxTech-SOC”
- Select all categories
- Archive to a storage account
- Select the storage account created earlier: “foxtechsoc”