Overview
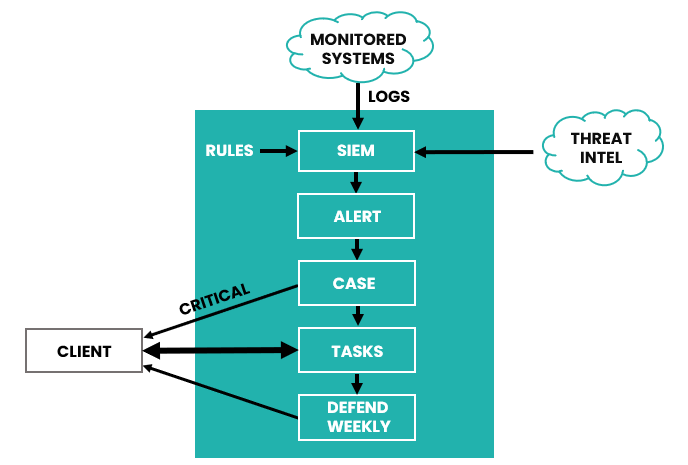
FoxTech DEFEND constantly monitors your IT for attacks, contains the threats and provides pragmatic advice on what to do next. Here’s a straightforward overview of how the service operates:
-
Data Collection: An agent installed on servers and laptops continuously sends log files to the DEFEND platform. Network devices send logs via Syslog and DEFEND fetches audit logs from your cloud services. These logs provide a comprehensive view of system activities.
-
Alert Generation: Upon receiving log data, DEFEND uses advanced rules and the latest threat intelligence to analyze and detect potential security issues. This process results in the creation of Alerts and potentially an Instant Response, such as blocking the source IP address.
-
Alert Analysis: Our Security Operations Center (SOC) team reviews these Alerts and group these into Cases to track the detailed investigation.
-
Case Management: Each Case is triaged and analysed, with specific Tasks being created to address and mitigate the identified risks. These Tasks describe corrective actions necessary to secure your systems.
-
Communication: You will be promptly notified via email when a Task is assigned to you. Updates on ongoing Tasks can be submitted either through the DEFEND Console or by replying to the email notifications. These can also be passed to your own ticketing system.
-
Escalation Procedures: For Cases of critical severity, our SOC team will escalate the issue directly to your designated primary contact to ensure swift action.
-
Reporting:
- Weekly Reports: These updates include details on Cases investigated, current vulnerabilities identified per device, and software packages affected by these vulnerabilities.
- Quarterly Reports: Every three months, a detailed report is sent out to provide an in-depth review of the security landscape and the effectiveness of the measures taken.
Through FoxTech Defend, we aim to provide you with a proactive, transparent, and effective defense mechanism, ensuring that your systems are secure and compliant.